UPDATE: April 12, 2024
Sisense has released additional guidance to customers regarding the incident beyond urging customers to reset API keys, tokens, and credentials used within Sisense application.
Sisense urged clients to specifically:
- Change all passwords associated with my.sisense.com
- Reset credentials in client-controlled databases and data model connection strings used within Sisense applications and services (https://docs.sisense.com/main/SisenseLinux/introduction-to-data-sources.htm?tocpath=Data%20Sources%7CConnecting%20to%20Data%20Sources%7C_____1)
- Reset any active User Param features (https://docs.sisense.com/main/SisenseLinux/personalization-parameters-for-live-data-sources.htm)
- Reset credentials leveraged for Active Directory synchronization (https://docs.sisense.com/main/SisenseLinux/Integrating-Active-Directory.htm)
- Rotate credentials for GIT integrations exposed to Sisense applications and services (https://docs.sisense.com/main/SisenseLinux/introduction-to-sisense-git-integration.htm)
- For B2D customers, leverage the API patch at api/v2/b2d-connection to update the B2D connection(https://docs.sisense.com/main/SisenseLinux/configuring-b2d-in-sisense.htm#Enabling)
- Rotate all keys associated with Sisense used within Infusion Apps (https://docs.sisense.com/main/SisenseLinux/enabling-infusion-apps.htm)
- Rotate all Web Access Tokens (https://docs.sisense.com/main/SisenseLinux/using-web-access-token.htm)
- Rotate all custom Email server connection credentials (https://docs.sisense.com/main/SisenseLinux/custom-email-servers.htm)
- Reset any secrets that appear in custom code Notebooks (https://docs.sisense.com/main/SisenseLinux/using-notebooks.htm)
For Non-SSO Clients:
- Reset the Secret in the Base Configuration Security section with your GUID/UUID
- Reset all Sisense application passwords. (https://dtdocs.sisense.com/article/connection-definitions)
- Force logout of all active sessions by sending a request from an Administrator account to the API endpoint /authentication/admin/logout_all_users (https://sisense.dev/guides/restApi/v1/?platform=linux&spec=L2023.11#/authentication/logoutAllUsers)
For SSO Clients
- For clients using SSO JWT for Sisense authentication, clients are required to update their sso.shared_secret and generate a new SSO handler (https://sisense.dev/guides/accessSecurity/jwt/)
- Rotate x.509 certificate for SSO SAML provider (https://docs.sisense.com/main/SisenseLinux/single-sign-on-using-security-assertion-markup-language-20.htm)
- For clients using OpenID, clients are required to rotate the client secret (https://docs.sisense.com/main/SisenseLinux/single-sign-on-using-openid-connect.htm)
ARC Labs and Binary Defense are actively monitoring a compromise of data associated with Sisense, a company that provides data analytic product and services. At this point, it is unknown if the Sisense’s network was compromised but independent researchers and government organizations indicate that data impacting Sisense has been discovered outside of an authorized space. Given the design of Sisense business model which provides companies the ability to integrate data analytics into various product and services in a modular fashion, the potential data exposure could be larger than those who directly work with Sisense.
The Sisense platform is designed to integrate customized analytics into applications, products, and services. Sisense also offers an SDK enabling developers to integrate Sisense analytics into various technology, tools, and platforms.
According to the Sisense website, Sisense has partnerships with various large software and product vendors indicating that organizations may be impacted by this data compromise through the integration of Sisense by a vendor into their product and services potentially.
As new information is released regarding the incident, ARC Labs and Binary Defense will make updates.
Recommend Immediate Action:
- Perform an investigation to determine whether your organization uses Sisense directly or indirectly through an integration/implementation within a third-party product or service.
- Reset any Sisense credentials (passwords, api keys, tokens, etc), including customer/partner portal access.
- Reset credentials (passwords, api keys, tokens, etc) to any product/service that leverages or is exposed to Sisense services.
- If you are using Sisense directly or indirectly, perform an audit of April activity associated with the user accounts and identities exposed to Sisense services and investigate any suspicious activity.
Sources:
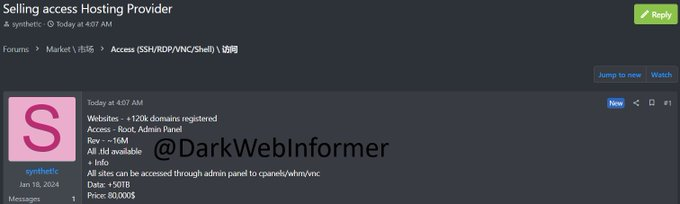
@DarkWebInformer – alleged threat actor is selling root access to the panel containing 50TB of Sisense related data for $80,000
References:
https://www.cisa.gov/news-events/alerts/2024/04/11/compromise-sisense-customer-data