A message board or an internet forum is an online discussion site where users can communicate with the entire group of members via posted messages. These are different from chat rooms where small groups send short messages, because forum posts are often longer than chat messages and typically organized into discussion topics. These forums are used for various topics such as hacking, selling stolen data, offering services to other users, advice on how to avoid identification by law enforcement, or simply technical questions and answers. The majority of the users use these forums to solve their problems, and they get assistance from other members who are more experienced with the topics. While many of the discussions are the same, some of the trending discussions on forums such as Raidforums, Hell Bound Hackers (HBH), Hack Forums, and Cracked.io can be found below.
Raidforums
Raidforums is a marketplace and a database sharing forum with some users offering exclusive data leaks. With over 445,000 registered users participating in discussion topics dedicated to technology, database leaks, and hacking, it is a high-profile forum. Most of the users on this forum discuss their issues throughout all phases of their operations, from initially breaking into servers to getting data out and selling it.
Trending on Raidforums:
Is it possible to get coverage of dark web data?
One question that frequently appears on Raidforums is how to find resources that are available on the Dark Web. Because search engines such as Google and Bing don’t index sites on the Dark Web, people rely on forum posts and word-of-mouth to find services instead. Users on Raidforums can add lists of resources, including chat applications, networks, marketplaces, and files. These user-curated lists identify new marketplace and sites to deliver the most comprehensive and widest coverage of Dark Web data in the industry.
As mentioned in the description of Raidfourms, many users often post stolen data and “leaks” to the site. These can be for sale or simply just posted in an attempt to give other threat actors the ability to use the data for malicious purposes. Some examples of users posting stolen data or ransomware victim lists to Raidforums can be found below.
This user posted a sample of a ransomware victim list that included employee email and password combinations from a well-established company.
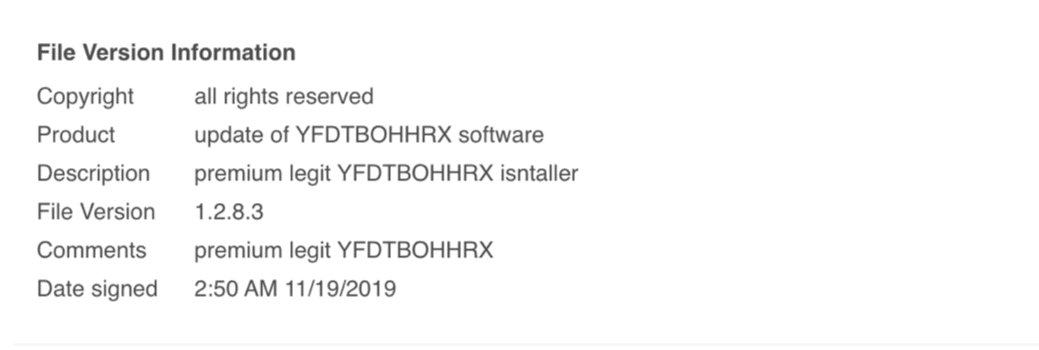
Another user is offering to sell the database of a popular Chinese chat application.
It is important for Binary Defense analysts to monitor sites like these in the event that our clients’ data may be leaked or appear for sale. If we find important information that could be used to harm our clients and their employees, a report documenting our findings and suggestions for the business will be sent to them immediately.
Hack Forums
Hack Forums is used by many in an attempt to learn the art of hacking, and less for posting stolen data like some of the others. Its users tend to be younger, with a curiosity about hacking and what they can do with it. Newer users often seek guidance from those that claim to be more experienced. Hack Forums has a reputation for being impenetrable to outsiders as well as being a harbor for trolls and brazen criminal activity.
Trending on Hack Forums:
How to gain unauthorized access to a computer network?
On Hack Forums, many users who are newer to hacking ask the more advanced hackers basic questions about how to break into computer networks. Some forum users ask this question many times as they get started. This reveals an aspect of cyber security threats that is important to understand: many people around the world have the motivation to get into cybercrime because they’ve heard it is lucrative or feel that it would be interesting, but lack the skill, aptitude or motivation to learn on their own, and instead rely on others to provide easy-to-use software or services. This has resulted in a thriving underground service-based economy. Vendors offer malware-as-a-service, phishing kits and phishing hosting services, keylogger and password stealing malware, compromised remote desktop (RDP) access to companies, databases of email addresses and passwords compiled from past breaches, software programs that make it easy to check passwords on many websites quickly, and many other turn-key solutions for aspiring cyber criminals. When eager and reckless newcomers to hacking purchase access to powerful tools and services, the threat to businesses increases – but at the same time, studying the patterns of attack associated with those criminal services and tools can lead to better detection and defenses if kept up to date.
Is hacking legal?
This question is often asked by new forum members, and they get a variety of answers to this question from the more experienced users. Some say that hacking that gains unauthorized access to a computer network or system is illegal, but the forum helps users understand the cybersecurity laws. Others describe hacking more generally as a part of computing and point out that it is a multifaceted discipline that covers a wide range of topics. Some users say that it will not harm a computer to steal sensitive information available on the computer. Others define hacking as a way to demonstrate to corporations that their security is lacking and perhaps teach them a hard lesson that they should focus more on security to protect their customers. It is safe to say that people with aspirations to profit from criminal hacking can always find a group of like-minded people who either help them justify their actions as acceptable or convince them that they will not suffer any consequences from their exploits.
Which network tools are used for researching targeted networks?
The majority of the users have discussed how to gather information about the networks of companies they are targeting using basic system tools including Netstat, Tracert, Ping, Nslookup, Telnet, and many more. Online services that provide scan data such as shodan.io, binaryedge.io and others are also frequently used to profile a targeted network from the outside and discover exposed services on a range of IP addresses. Most network profiling is for the purpose of finding remote access facilities such as SSH, RDP, Telnet or FTP and then launching password guessing brute-force attacks against them. More advanced attackers specifically scan for vulnerable servers that have not been patched and can be exploited. One thing that is clear from forum discussions is that working zero-day exploits are very rare, are sold for very high sums of money, and usually only offered in private sales. Most widely used exploits are for vulnerabilities that have been patched for some time, targeting companies that have failed to apply security patches to public-facing servers.
Hellbound Hackers (HBH)
Hellbound Hackers is another site that attempts to educate those new to the world of illegal internet activity. What you’ll find when visiting this site is many users giving descriptions of different attack methods or tools that can be used to carry out attacks.
Although not everything on the site could be considered harmful, educating aspiring hackers could very well lead to harmful activity and that’s why this site could be considered dangerous.
A user on HBH has posted what they consider to be the most useful and common ways to “hack a website.” Included under each of the methods are resources or sites that can be visited to teach others how to carry out the attacks. While there is a lot of misinformation in the post, this can still entice those who are still learning to look more into the methods, leading to more attempts and opportunities for them to be carried out in the future.
Cracked
Cracked is another site that is used to distribute or sell stolen data obtained from threat actors.
Although the forum advertises itself as a learning resource for penetration testing, forum users have asked for help with sending out mass email to employees of banks and said they would pay someone in bitcoin to send emails for them. Other forum members asked for advice to commit refund fraud against stores, and the site advertises software for using large lists of passwords to break into other people’s email accounts in mass quantities.
Retail businesses will often offer incentives such as reward codes or cash vouchers to their customers that frequently shop their products. These codes or vouchers can often be stolen or duplicated and sold on Cracked for a profit. It is imperative these businesses are alerted to these postings and if possible, our analysts will give more insight on how the threat actors may have obtained them.
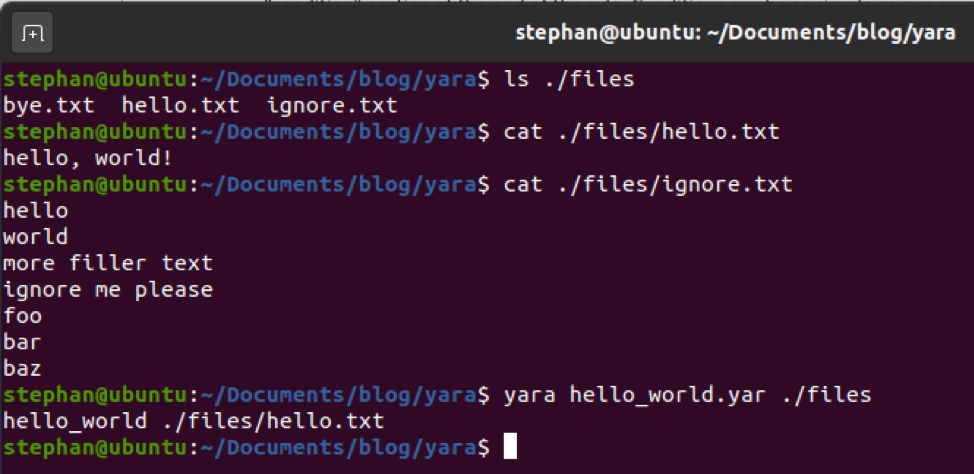
Many of the posts will contain a link to the seller’s Shopify account where codes and vouchers for other businesses can be found as well. A method to make it more difficult for the threat actors to sell the codes would be to report the Shopify account and attempt to have it taken down.
Conclusion
Let’s be perfectly clear: breaking into computers, networks, email accounts, websites or any other system that belongs to someone else without their explicit permission is illegal and wrong, regardless of the motives of the person breaking in. Binary Defense does not condone using hacking forums for criminal activity. Instead, we recommend that people who want to learn or improve their offensive security skills should first look into resources and communication channels in the Information Security community where criminal activity is not tolerated. For example, TrustedSec has a Discord server that is free and open to all, filled with friendly and helpful experts and learners discussing professional hacking skills. There are productive and useful ways to use hacking skills to do good and enhance the security of systems when the company that owns the assets has authorized those actions clearly in writing.
For security professionals, there is a great deal of value in paying attention to the discussions happening on these forums or subscribing to a security service such as Binary Defense’s Counterintelligence service, which keeps an eye on these forums for you and your company. Knowing what hacking tools are offered for sale and how they work can help defenders craft defenses that are designed to detect if those hacking tools are used against their network. Watching the sale of stolen passwords and dumped databases can provide an early warning that a company’s data has been stolen and will soon be used for fraud, if someone buys the data. Simply understanding what sort of data has the most value on underground marketplaces can help companies prioritize defenses to protect the data that is most likely to be targeted for theft. Some of the technical discussions on the forums have nothing to do with questionably legal activity and are useful to learn from. Even the advertisements for criminal services and the lists of resources on the Dark Web are helpful to understand emerging threats and add new Dark Web sites to be monitored for stolen data and information stolen from companies. Binary Defense dedicates analysts every day to monitoring forums in multiple languages and keeping up with the information shared and watching out for any data having to do with our clients and their industries. Our clients count on us to keep them well informed about current threats and forewarned if any mention of their company’s brand, data or people appear on these sites.