BD Platform
Security Operations, Accelerated.
UPDATE: April 12, 2024
Sisense has released additional guidance to customers regarding the incident beyond urging customers to reset API keys, tokens, and credentials used within Sisense application.
Sisense urged clients to specifically:
For Non-SSO Clients:
For SSO Clients
ARC Labs and Binary Defense are actively monitoring a compromise of data associated with Sisense, a company that provides data analytic product and services. At this point, it is unknown if the Sisense’s network was compromised but independent researchers and government organizations indicate that data impacting Sisense has been discovered outside of an authorized space. Given the design of Sisense business model which provides companies the ability to integrate data analytics into various product and services in a modular fashion, the potential data exposure could be larger than those who directly work with Sisense.
The Sisense platform is designed to integrate customized analytics into applications, products, and services. Sisense also offers an SDK enabling developers to integrate Sisense analytics into various technology, tools, and platforms.
According to the Sisense website, Sisense has partnerships with various large software and product vendors indicating that organizations may be impacted by this data compromise through the integration of Sisense by a vendor into their product and services potentially.
As new information is released regarding the incident, ARC Labs and Binary Defense will make updates.
Recommend Immediate Action:
Sources:
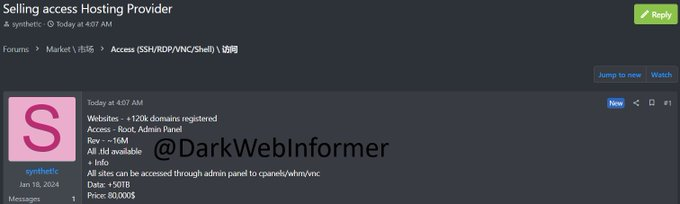
@DarkWebInformer - alleged threat actor is selling root access to the panel containing 50TB of Sisense related data for $80,000
References:
https://www.cisa.gov/news-events/alerts/2024/04/11/compromise-sisense-customer-data