BD Platform
Security Operations, Accelerated.
Russia’s invasion of Ukraine increased malicious cyber activity among hacktivists. Several criminal hacking groups supportive of Putin’s regime have transformed themselves from criminal service providers into hacktivist groups. This change occurred as a response to the unprecedented global sanctions imposed on Russia as well as the material support to Ukraine provided by the United States and its partners.
Russian hacktivists do not focus on financial gain; they are working to advance political and societal causes. Hacktivist organizations are motivated by patriotic principles and have been used by Russia and other governments as a resource during military confrontations. While the government may use and influence the direction of hacktivist groups, they have been notoriously difficult to control, with members often substituting their own judgment in place of any formal direction about what to target. Hacktivists are aware and sensitive to current events on the battlefield as well as on the geopolitical front and respond to them almost in real-time.
The Number of Pro-Russian Cyber-Groups Engaged in the War Is Increasing
According to CyberKnown, a group that provides Open Source Intelligence (OSINT) investigations and geo-political awareness reports, since the war began, the number of cyber groups engaged during the war has been changing dramatically. The number of pro-Russian cyber groups was initially lower than pro-Ukrainian until September 2022.
| Date | Support Ukraine | Support Russia | Unknown |
| 2/28/2022 | 11 | 6 | 1 |
| 3/5/2022 | 39 | 13 | 3 |
| 4/4/2022 | 48 | 23 | 3 |
| 5/1/2022 | 48 | 30 | 2 |
| 8/8/2022 | 45 | 43 | 5 |
| 9/7/2022 | 35 | 43 | 5 |
| 10/12/2022 | 36 | 42 | 6 |
| 11/28/2022 | 36 | 40 | 5 |
Table 1. The number of Hacktivist Groups Aligning with Russia or Ukraine since the February invasion, courtesy of CyberKnown.
Binary Defense analysts have seen a significant increase in groups supporting Russia, from 6 to 43, in a short period of time. It is possible that there was less support for Russia at the beginning since malicious actors hoped for a quick victory, and later, realizing that the goal was not reachable, they focused on helping Russia more. Binary Defense Analysts also assess that some groups may be under the influence of the Russian authorities and have been forced to cooperate since the war started. This assessment is based on the fact that several cyber criminal groups were arrested by Russian authorities just prior to the invasion, and past events as well as leaked chat logs of cybercriminals support the conclusion that Russian government authorities have compelled cybercriminals to cooperate in return for release from prison.
However, most groups are based in Russia, are very patriotic, and support the efforts of Russia willingly. Analysts have seen an increase in Distributed Denial of Service (DDoS) and data-leakage attacks targeting governments, critical industries, and organizations in Ukraine and Western countries.
KillNet was created in November 2021 and offered a tool to launch DDoS attacks. However, after the war started, the gang transformed from a criminal service provider to a hacktivist group.
In May 2022, KillNet officially declared cyber war against the United States, the United Kingdom, Germany, Italy, Latvia, Romania, Lithuania, Estonia, Poland, and of course, Ukraine. Since the war started, we have seen an increase in DDoS attacks targeting governments, critical infrastructure, and organizations based in those countries.
The group seeks revenge for wrong doings they believe the west has committed against Russia, and they immediately respond. For example, in June 2022, they attacked 1,652 Lithuanian online resources in retaliation for Lithuania’s blockade preventing goods from passing to Kaliningrad. In September, it was reported that hackers had declared cyber war on the Japanese government too, accusing it of conducting an anti-Russian campaign. In August, KillNet brought down the website of the Information Technology Service of Moldova in response to the criticism expressed by the Moldavian authorities in relation to the war in Ukraine.
From February to September, the group mainly concentrated on targeting EU-based countries, but in a recent interview given by KillMilk, the founder of KillNet, he announced that they have started concentrating on US-based companies. "For eight months, we have been learning and breaking Europe while the US has been preparing to meet with us. We are just starting to attack the territory of America's cyberspace," stated the hacker.
In October this year, KillNet launched multiple attacks against US airports as well as state government websites in Kentucky, Mississippi, and Colorado. Recently, KillNet claimed to have targeted several FBI websites and the website of the White House.
On November 18, KillNet, in cooperation with other hacking groups, claimed responsibility for the attack on the Starlink Service provider. The group stated on their Telegram channel that access to Starlink was denied to subscribers for several hours. The Ukrainian military has commonly used Starlink as a mobile internet service provider during the Russian invasion. It is critical for the Ukrainian military and volunteer defense units on the frontlines to have access to the internet.
The group has 92,000 followers on their Telegram channel, which encourages the gang to continue launching additional attacks. They use a wide audience to promote their ideas and attract more hackers. In September 2022 they made an announcement that 14 new hacking groups have joined the KillNet hacking collective.
The group has a well-organized command structure, which allows them to launch coordinated attacks. KillNet consists of multiple “specialized squads,” the main one has been dubbed Legion. Different small squads are organized around Legion and its leader. Before an attack, instructions are sent to the commanders of each squad. This decentralized approach helps the group more efficiently organize attacks.
Among all cyber-attacks launched by pro-Russian groups, the one that garnered the most attention was an attack on Lockheed Martin, an American defense corporation.
The hacker called KillMilk declared war against Lockheed Martin as a retaliation for the HIMARS systems supplied by the U.S. to Ukraine. KillMilk is the founder of KillNet, but to “protect” the gang, KillMilk left the hacktivist group and immediately launched the DDoS attack on Lockheed Martin claiming credit as an individual, rather than involving KillNet. The hacker claimed to have stolen information from Lockheed Martin, but Lockheed Martin denied that any of its systems had been compromised.
On November 13, the anniversary of the hacking group, KillMilk posted a patriotic message:
“Before a special military operation, we left the darknet space and joined the Russian mission. Everything we have done since the very first day is only for the sake of helping our country. Maybe that's the only thing that makes us different.”
XakNet Team is a hacktivist group that became known when the war started. In an interview, an associate of the group claimed that before the war its members were IT service providers, but since February 24, they have become hacktivists. The group announced support for the Kremlin’s position and immediately launched attacks against Ukrainian entities.
Recently, XakNet group gained access to the Ukrainian Ministry of Finance. In response to the attack, Dmitry Gusev, a Russian State Duma deputy, proposed assigning military ranks to Russian hackers.
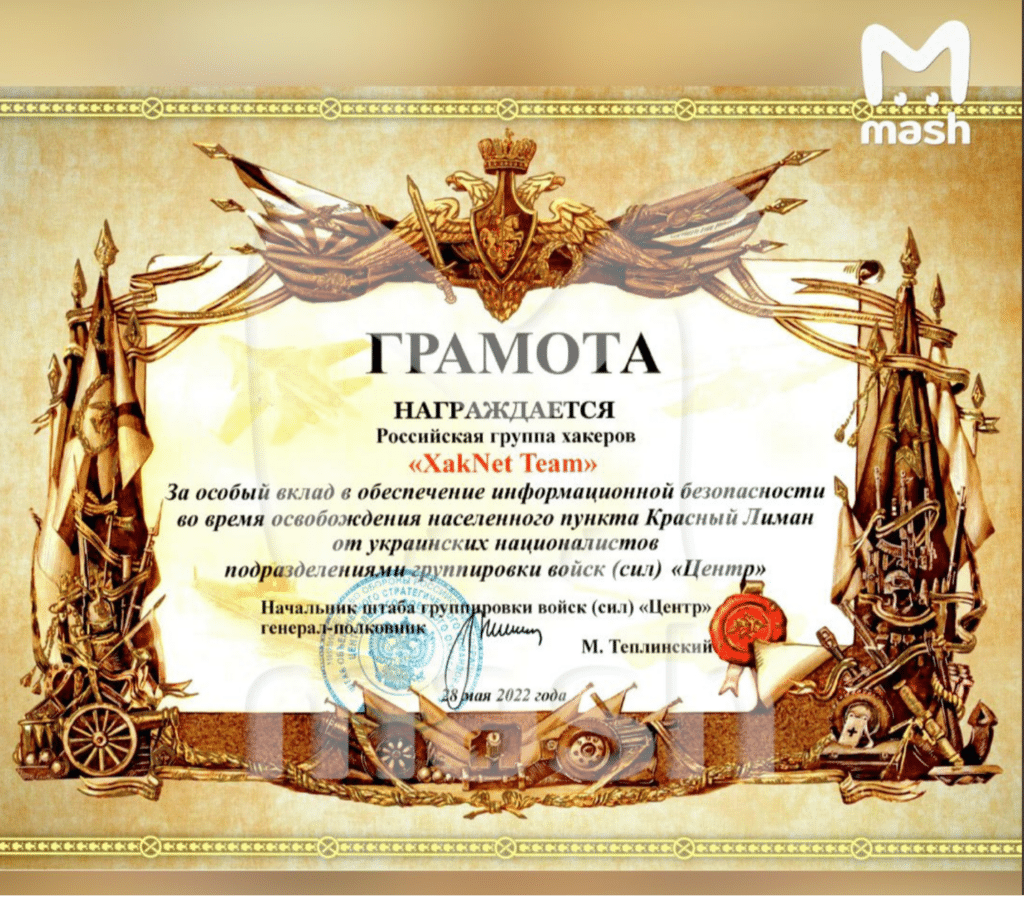
Hacktivists from the Russian XakNet Team also took down the servers of the Ukrainian surveillance and guidance system "Kropiva." They believed that the blockade helped to significantly reduce the capabilities of the Ukrainian army on the front line. They earned a certificate of appreciation from the Russian Colonel-General.
Pro-Russian hacker "Joker DNR" claimed to get access to the DELTA program, a system for receiving, evaluating, and displaying information on enemy troops, coordinating defensive forces, and providing situational awareness in real time. The program complies with NATO requirements, and it is actively used by Ukrainian forces.
The hacktivist published screens of the program on his Telegram channel on November 1, but the attack was not confirmed by Ukrainian officials.
Andrey Baranovich, a Ukrainian cybersecurity expert, said that a few accidents happened in August when hackers used a phishing attack to get access to users’ accounts. According to Baranovich, hacking attempts against DELTA will continue.
OSINT analysis indicates an increase in DDoS and data-leakage attacks targeting governments, critical industries, and organizations in Ukraine and Western countries. Very often, hacktivist groups come together to launch attacks. For example, the leader of the hacktivist group Zarya, Hesh, claimed to launch an attack on the Ukrainian Security Service in cooperation with other groups, such as Bereginya and XakNet.
KillNet and hacker groups Msidstress, Radis, Anonymous Russian, Mirai, and Halva have claimed responsibility for the DDoS attack targeting Starlink.
Pro-Russian hacktivist groups have become more organized and have started to cooperate, as they share the same goal. This will help them to launch more impactful and destructive attacks in the future.
Over the past year, former cybercriminals driven by the same ideology supporting Russia have transformed into hacktivists. Russian hacktivists promote campaigns to highlight and publicize their successes on their Telegram channels and media outlets to attract more members.
Hacktivist groups no longer include a few random individuals who can launch minor DDoS attacks or disrupt small websites. There is now coordination by these groups to conduct large-scale, planned DDoS attacks against their targets while maintaining active public relations campaigns. Organizations and governments should consider these activities as a sufficient warning.
Analysts at Binary Defense will continue to monitor Russian Telegram channels, underground forums, social media and other sources for new developments in this topic.
Written by: Nataliia Zdrok, Threat Intelligence Analyst at Binary Defense