BD Platform
Security Operations, Accelerated.
You’ve already invested in Palo Alto Network’s Cortex XDR or XSIAM platform. But tech alone doesn’t stop attackers. Binary Defense transforms your Cortex deployment into a 24/7 threat detection and response powerhouse—fueling it with behavior-based detections, continuous threat hunts, and expert human analysis that doesn’t miss.

Attackers don’t wait for alerts and they don’t follow playbooks.
Cortex XDR and XSIAM offer visibility, correlation, and automation. But most security teams don’t have the time, staffing, or experience to fully operationalize the platform. That leaves blind spots, and attackers exploit them.
Binary Defense helps you:
This isn’t about more alerts. It’s about better decisions, faster action, and fewer incidents.
We bring the attacker’s mindset to your Cortex environment—enhancing signal, surfacing behavior, and delivering response outcomes.
We securely integrate with your Cortex XDR or XSIAM instance and evaluate detection coverage, telemetry health, and visibility gaps.
We map your telemetry to MITRE ATT&CK, writing personalized rules and enriching alerts with threat intel, context, and severity scoring.
Our 24/7 SOC monitors alerts and suspicious behavior in real-time—triaging signals, running playbooks, and investigating with a human-led lens
We combine data across identity, endpoint, network, and cloud—linking attacker behavior across stages to build the full story.
Our threat hunters proactively look for signs of compromise based on threat intel, malware trends, and hypotheses tested in your data.
We run coordinated response actions via Cortex, contain hosts, disable accounts, trigger automation workflow, and hand you needed evidence and response steps.
Whether you want to fully outsource or stay hands-on, we operate as an extension of your team, with shared channels, access, and workflows.
We provide continuous tuning, detection engineering, and feedback loops based on threat trends and incident learnings

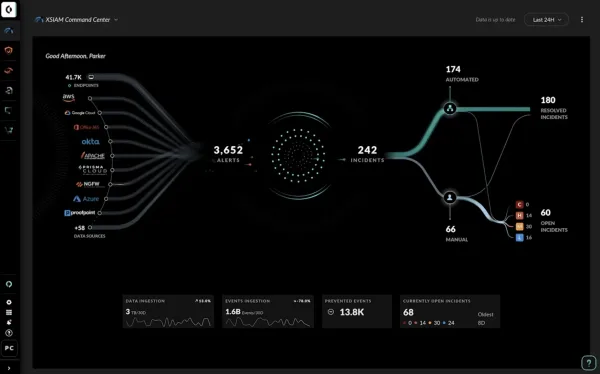
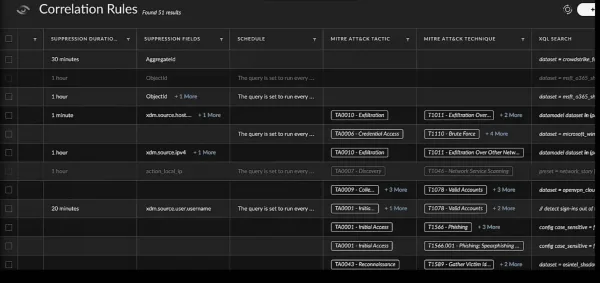
Let’s Make Cortex Work Harder for You.