BD Platform
Security Operations, Accelerated.
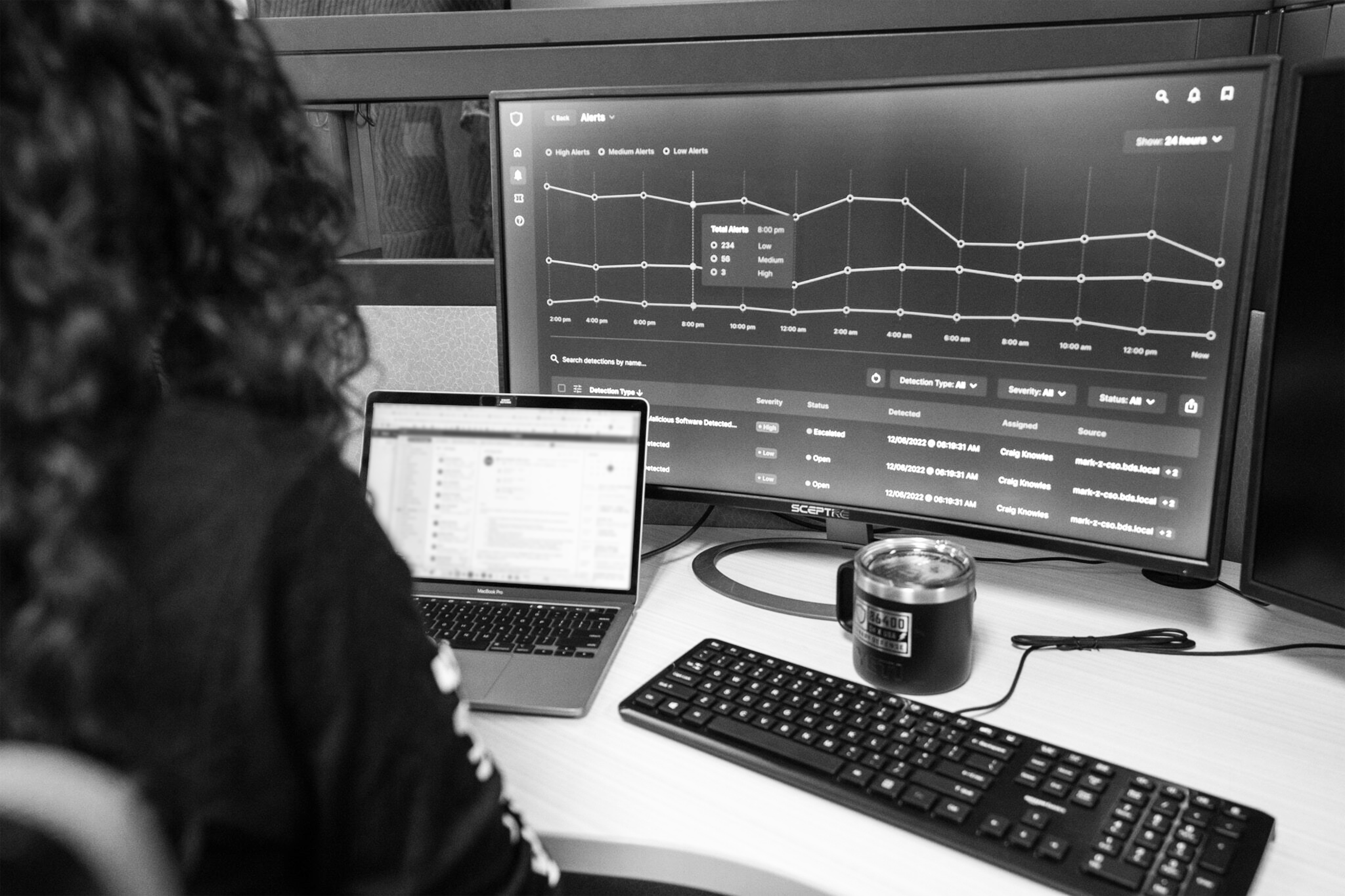
Stop threats before they succeed with a detection engine built on behavioral analysis, deception technology, and real-time disruption without impacting legitimate business operations.
Attackers study EDR systems and design ways around them. Once they bypass, they move fast—stealing data, hijacking identities, and spreading laterally.
BD Vision shuts them down with:



Capabilities built to expose evasions, mislead attackers, and stop threats cold.
Spots patterns that signatures miss
Closes gaps attackers exploit
Turns attacks into intelligence
Host isolation & identity lockouts
Technology alone isn’t enough. Every BD Vision alert is monitored, validated, and responded to by Binary Defense’s 24/7 SOC and detection engineers. That’s the difference between knowing about a threat and actually stopping it.
