BD Platform
Security Operations, Accelerated.
Adversaries continue to refine their tactics, techniques, and procedures. Recently, Binary Defense researchers in ARC Labs took a deep dive into a fresh DeedRAT sample, dissecting its infection chain, sideloading tricks, and persistence mechanisms. This post walks you through how DeedRAT infiltrates systems, how it sticks around, and most importantly, how defenders can spot and stop it in its tracks.
DeedRAT is a backdoor with a toolkit designed for stealth and control. Once inside a system, it can:
DeedRAT’s delivery method of choice? Phishing campaigns. These attacks are currently attributed to the Salt Typhoon threat group (also known as Earth Estries), a Chinese APT targeting government, telecom, and other critical sectors across the US, Asia, the Middle East, and South Africa. Since at least 2020, Salt Typhoon has been linked to targeted attacks against these industries and their supply chains.
Our analysis began with a sample delivered via a .zip archive containing three files:
The infection kicks off when MicRun.exe, which is a legitimate program that is part of the VIPRE Antivirus Premium suite, is executed. This triggers the sideloading of the malicious SBAMRES.dll, which then locates and executes the encrypted shellcode in SBAMRES.DLL.CC. The entire package is then copied to C:\ProgramData\MicroDefaults for further operations.
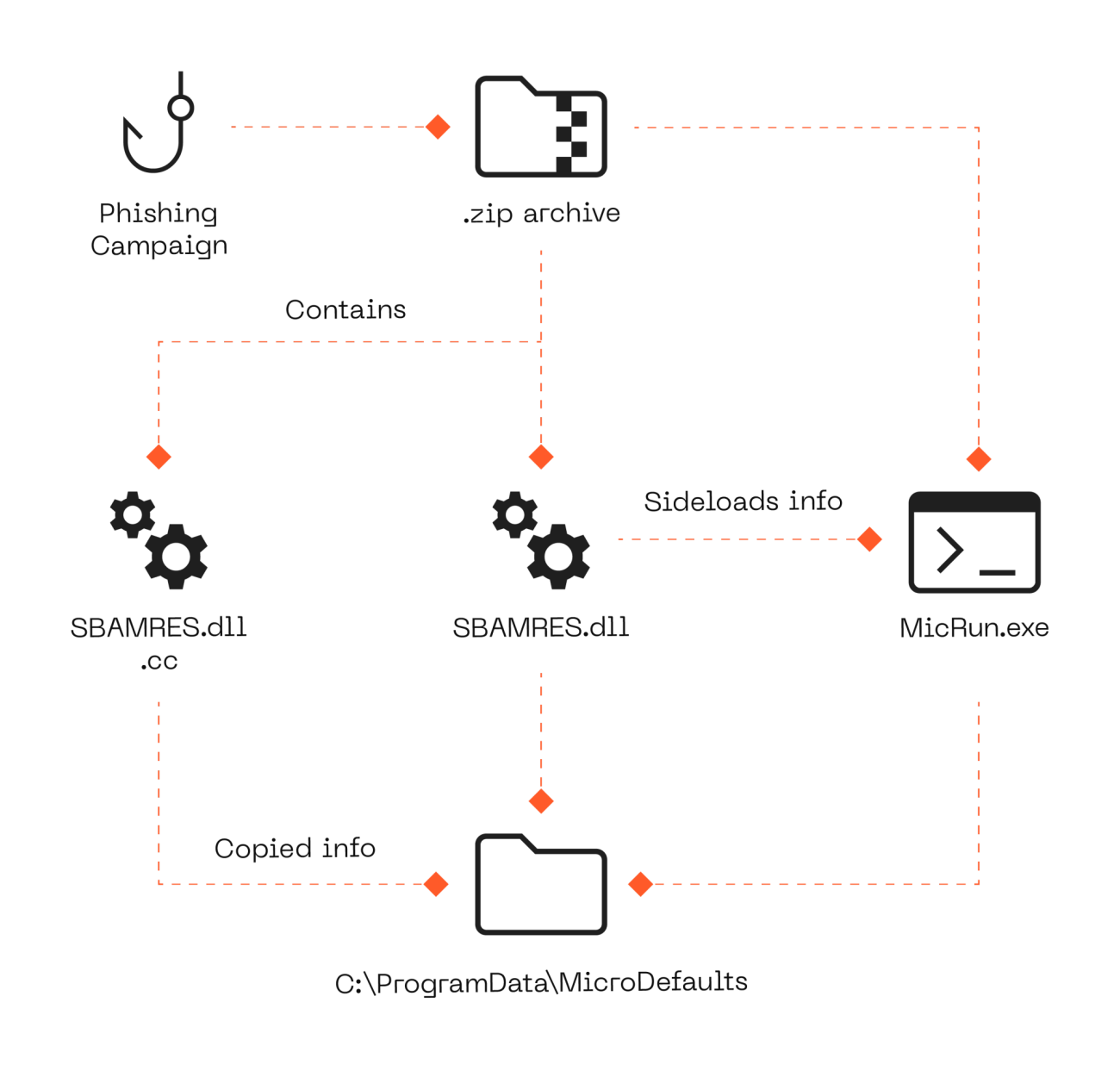
DeedRAT leverages DLL sideloading (https://attack.mitre.org/techn...) to slip past defenses. By exploiting legitimate applications that are vulnerable to DLL hijacking, attackers can load malicious code under the guise of trusted software. In this case, if Windows Side-by-Side (WinSxS) manifests aren’t strict, a malicious DLL can be loaded alongside a legitimate app, making detection much harder.
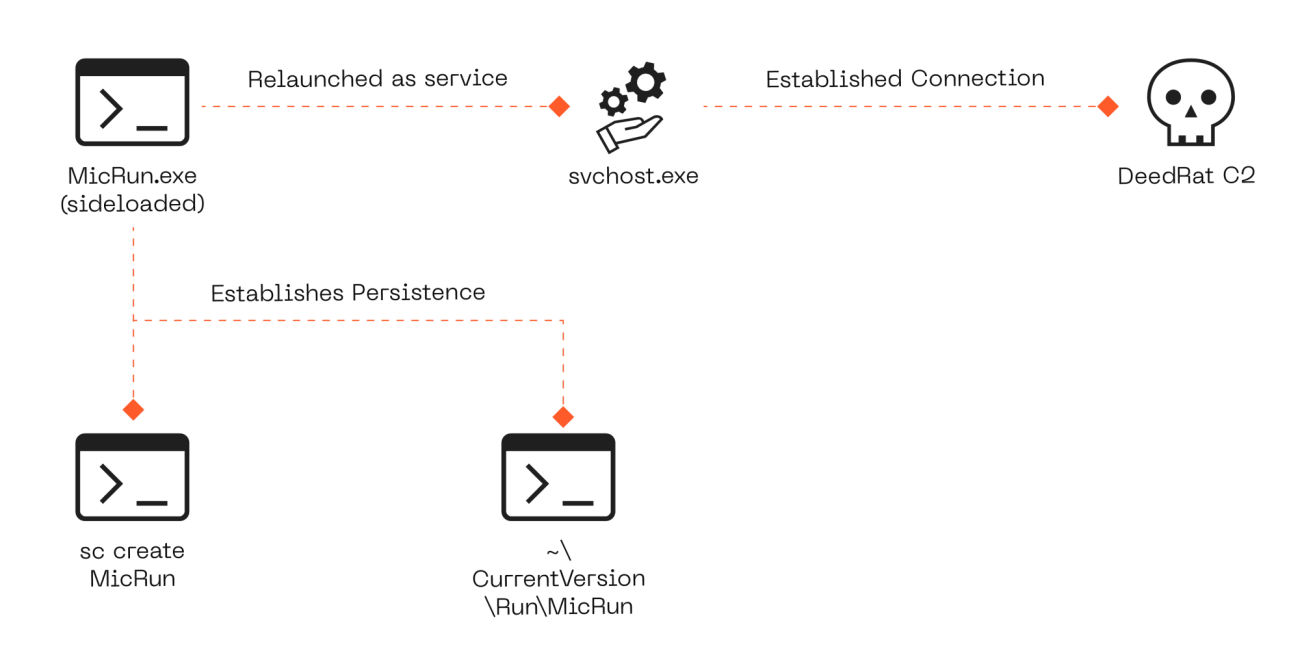
Once sideloaded, DeedRAT ensures it survives reboots and user logins through two redundant persistence mechanisms:
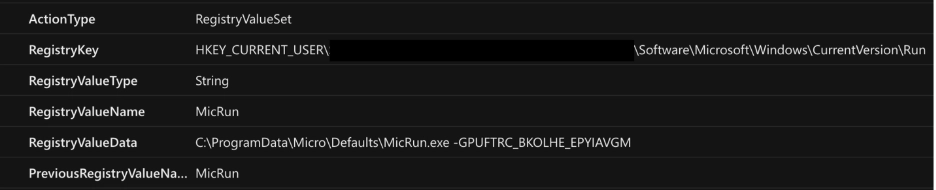
The malware creates a value under ~\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\MicRun, causing MicRun.exe to auto-execute at logon. An appended argument, matching a specific regex pattern, likely serves as a unique identifier for the infected machine or method.
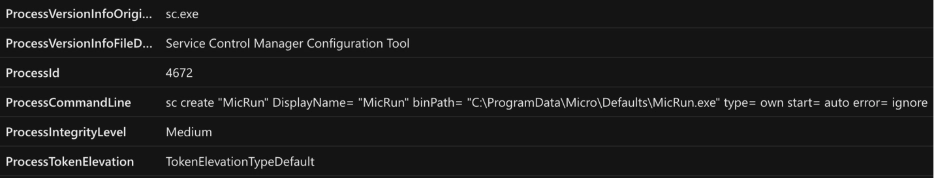
DeedRAT also creates a Windows service to launch MicRun.exe automatically:
sc create "MicRun" DisplayName= "MicRun" binPath= "C:\ProgramData\Micro\Defaults\MicRun.exe type= own start= auto error=ignore
These dual mechanisms provide redundancy so that if one fails, the other keeps DeedRAT alive.
After persistence is established, MicRun.exe is relaunched as a service via svchost.exe, which then attempts to connect to its command-and-control (C2) server at luckybear669[.]kozow[.]com over ports 80 and 443. During our lab analysis, the C2 server was offline, so no outbound connection was observed.
To defend against DeedRAT, Binary Defense recommends:
For actionable detection and threat hunting criteria, check out the ARC Labs GitHub repository.