BD Platform
Security Operations, Accelerated.
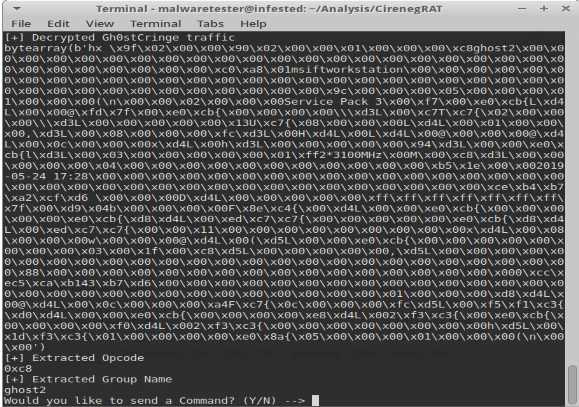
Malware communicating its login packet to my server
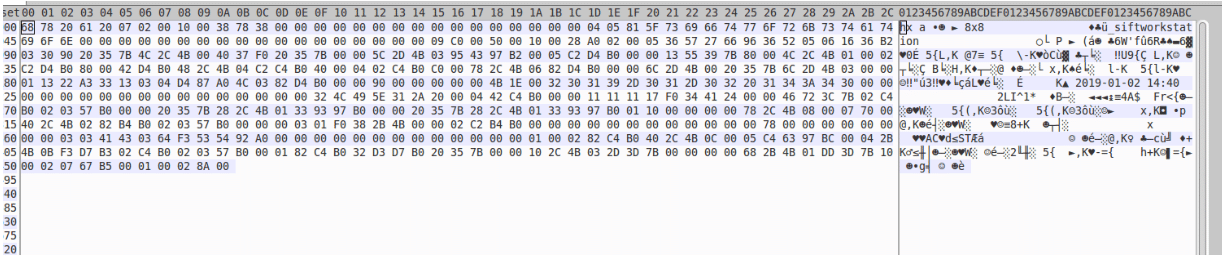 Some of the information stolen:
Some of the information stolen:
| Opcode | Name | Description |
| 0x00 | Shutdown | Obtains SYSTEM tokens and privilege and then shuts down the machine |
| 0x01 | Uninstall | Uninstalls itself using the Uninstall export |
| 0x02 | RegWorkRemark | Sets a registry value in its service key called “Remark” to null |
| 0x03 | ObtainInfoAndSendToC2 | Obtain Computer Info and resend to C2 |
| 0x04 | ChangeGroup | Changes malware Group ID |
| 0x05 | CleanEvent | Locate and Delete Event logs |
| 0x06 | DownloadNewModule | Connects to C2 server and downloads and executes a new module |
| 0x07 | Update | Connects to C2 server and downloads, executes, and updates new module |
| 0x08 | OpenUrlShow | Leveraging iexplorer.exe, open a supplied URL, showing it to the victim |
| 0x09 | OpenUrlHide | Leveraging iexplorer.exe, open a supplied URL covertly. |
| 0x0A | ExecuteNewWithCommands | Create a new file and then execute it with specific commands, which are supplied by the C2. |
| 0x0B | PopupMessage | Use SendMessageBox to send a popup message to the user. |
| 0x0C | ProcessEnum | Using createtoolhelp32snapshot to search for all open processes, which is then sent back to the C2 server |
| 0x0D | EnumWindows | List open windows using EnumWindows |
| 0x0E | OpenProxy | Loads a new dll that contains the export “OpenProxy” from memory into a new memory buffer. Then, locate the function in the dll exports and call it. |
| 0x0F | CloseProxy | Close the proxy, using the same dll used in OpenProxy. |
| 0x10 | Keylogger | Using the string “Load From Memory” and “Load From Memory --End” as text delimiters, Allocate memory and load a new dll from memory which contains the function “PluginMe”. |
| 0x65, 0x66, 0x67, 0x68, 0x69, 0x6A, 0x6C, 0x6D, 0x6E, 0x6F, 0x70 | KeyloggerAsThread | Do the above, however, load the PluginMe function as a new thread. |
| Opcode | Name | Description |
| 0x00 | Shutdown | Obtains SYSTEM tokens and privilege and then shuts down the machine |
| 0x01 | SvcInstall | Install the malware as a service |
| 0x02 | DownloadAndExecute | Connects to C2 server and downloads and executes a new module |
| 0x03 | DownloadAndSvcInstall | Connects to C2 server and downloads and executes a new module, which is then installed as a new service. |
| 0x04 | UrlOpenShow | Leveraging iexplorer.exe, open a supplied URL, showing it to the victim |
| 0x05 | UrlOpenHide | Leveraging iexplorer.exe, open a supplied URL covertly. |
| 0x06 | CleanEvent | Locate and Delete Event logs |
| 0x07 | RegKeyRemark | Sets a registry value in its service key called “Remark” to null |
| 0x08 | RegKeyGroup | Changes malware Group ID |
| 0x09 | SendMessage | Use SendMessageBox to send a popup message to the user. |
| 0x0A - 0x14 | Keylog | Using the string “Load From Memory” and “Load From Memory --End” as text delimiters, Allocate memory and load a new dll from memory which contains the function “PluginMe”. |
| Opcode | Use |
| 0xC8 | Login |
| 0xD4 | Process and Windows Response |
| 0xD5 | Configuration Response |
| Opcode | Use |
| 0xC8 | Login |
| 0xD5 | Process and Windows Response |
| 0xD6 | Configuration Response |
| Campaign | IP | Install Location | Mutex | Service Info |
| Indexsinas | Distro:14.31.36[.]202:8111, 1.indexsinas[.]me:8111 C2:dllhost[.]website:8093 | %SystemRoot%/System32/ | dllhost.website:8093:serviecs | Service: serviecs Service Display Name: System Remote Deta Simulation Layer Service Group: serviecs |
| MadoMiner | Distro: t.honker[.]info:8/ C2: sky.hobuff[.]info:8008 | C:usersPublicApplication DataDRM | sky.hobuff.info:8008:ctfmon | Service: ctfmon Service Display Name: System Remote Data Simulation Layer Service Group: ctfmon |
| IndoneMine | Distro: indonesias[.]me:9998 C2: http://indonesias[.]website:5814 | - | indonesias.me:9998:RpcEpt | Service:RpcEpt Service Display Name: Remote Access Routing Manager |
| Office.exe | Distro: 106.13.96[.]196 C2: 106.13.96[.]196:8090 | - | 106.13.96.196:8090:EventSystem | Service Name: EventSystem Service Display Name: Com+ EventSystem |