BD Platform
Security Operations, Accelerated.
At DefCon 33 this year offensive security testers and adversaries alike received a new tool in the form of GlytchC2. GlytchC2 is an open-source proof-of-concept C2 framework that leverages Twitch’s IRC chat and live streaming platform to perform covert command and control (C2) communication.
This blog covers how GlytchC2 operates and how defenders can detect it.
While attackers using web services for C2 communications is a tale as old as time, encoding data and sharing it via a live streaming service is not. Despite being in a proof-of-concept state GlytchC2 can easily be adopted and integrated by other malicious actors. This represents a step forward in the average attacker’s toolkit that necessitates a response from blue teams.
The GlytchC2 framework uses plaintext IRC over port 6667 to connect to irc.chat.twitch.tv, where attacker-issued commands are delivered through an attacker-controlled Twitch channel. This approach allows GlytchC2 traffic to blend in with normal streaming-related activity, making traditional detection methods less effective.
To achieve data exfiltration, GlytchC2 streams collected information via Twitch’s RTMP streaming service, effectively turning a live broadcast into a hidden outbound data channel. The attacker can then capture and decode the stream to extract the exfiltrated data. By using a mainstream platform as a relay, GlytchC2 highlights the challenges of distinguishing malicious use of public cloud and streaming services from legitimate traffic.
Binary Defense Researchers analyzed the provided proof-of-concept files in the BD malware lab, which yielded valuable insight into the telemetry generated by the C2 framework:
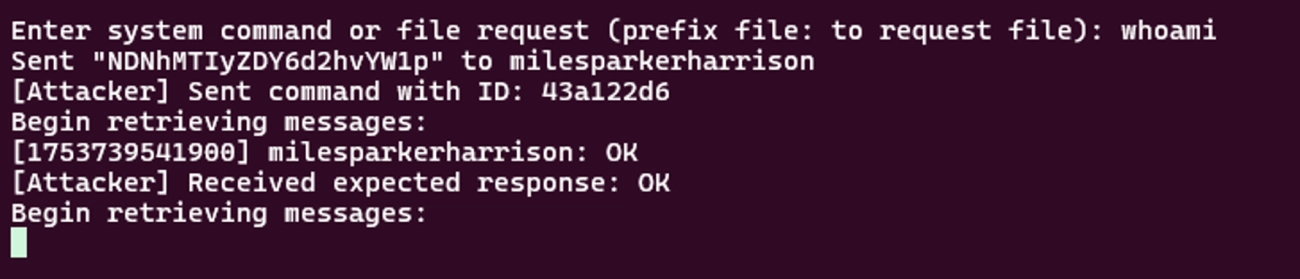
From this point, an attacker may provide any command as instructions for the victim host. Optionally, an attacker may use the `file:`prefix to request a specific file. Following execution of the whoami command in our example, the input is encoded and transmitted to a designated Twitch channel. The server component monitors this channel, decodes the input, and executes the associated command within the client environment:

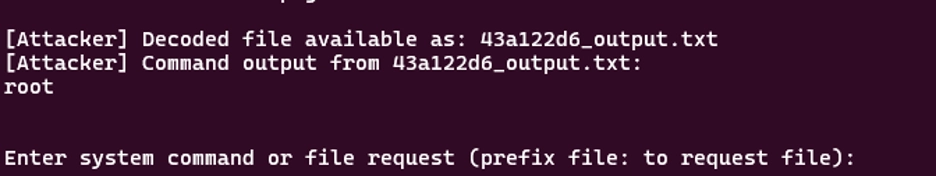
In response, the client application broadcasts a Twitch stream containing video frames embedded with encoded output data. These frames are decoded by the server application, resulting in the following observable response:
All communications between client and server generate unique network traffic. When intercepted using MiTMProxy, this traffic reveals detailed and distinguishable indicators of C2 behavior in the form of IRC welcome messages created by Twitch, as shown below:
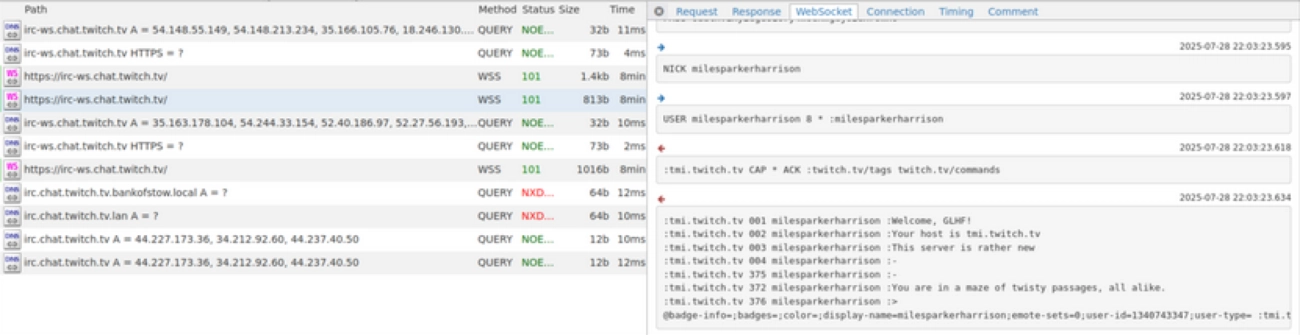
Correlating network traffic with endpoint logs provides the strongest points of detection for GlytchC2 style C2 Traffic. Defenders should focus on the following when threat hunting or developing detections for this project:
GlytchC2 highlights how adversaries have consistently adapted to hide in the noise of popular network traffic. For the average defender, success depends on spotting outliers amongst the noise, an achievable goal with the right tools.
We at Binary Defense will continue to analyze and publish findings on tools like GlytchC2 to give defenders the visibility and context they need to stay ahead of attackers.