BD Platform
Security Operations, Accelerated.
Binary Defense ARC Labs analyzed a recent payroll fraud intrusion at a healthcare provider that reflects a tactical shift in how these attacks are being carried out.
Ransomware may dominate headlines, but some of the most effective modern attacks don’t rely on malware at all. Instead, attackers are exploiting identity workflows, trusted access paths, and payroll self-service features to quietly steal money — one paycheck at a time.
ARC Labs recently investigated an attack where an adversary redirected an employee’s salary by modifying direct deposit information in a payroll platform after compromising the user’s identity account. The attack was technically simple, operationally precise, and deliberately low-noise.
This is not an anomaly. It’s a sign of where financially motivated attacks are heading.
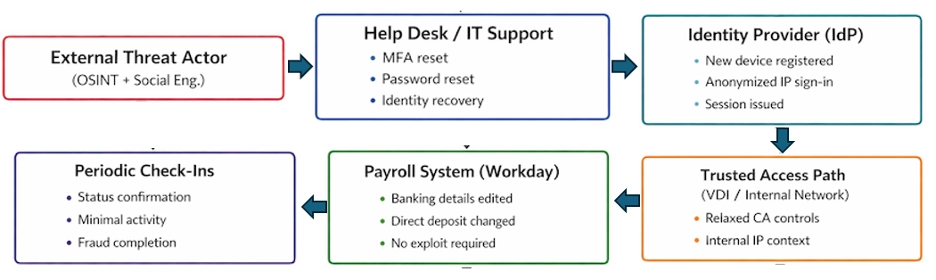
This attack was not invisible — but it was fragmented across systems that rarely talk to each other. When identity recovery, trusted access paths, and payroll self-service converge, attackers gain a low-noise path to direct financial theft.
This step is critical. Once MFA protections were weakened, the rest of the attack required no further deception.
After the reset:
From an identity provider perspective, these were “successful” logins — no exploit required.
Rather than accessing payroll directly from the internet, the adversary connected through a VDI environment that was implicitly trusted by downstream applications.
This mattered because:
Once inside the VDI, the attacker blended into normal user behavior.
The attacker logged into the payroll platform and:
Notably absent:
One of the most significant tradecraft shifts in this incident was the adversary’s use of virtual desktop infrastructure (VDI) as a trusted execution path to reach enterprise applications like Workday. Prior public reporting on payroll diversion and “payroll pirate” campaigns has largely focused on compromise through phishing or adversary-in-the-middle attacks to capture credentials/MFA, followed by direct access to SaaS platforms via single sign-on and abuse of mailbox rules or OAuth tokens to hide persistence and notifications. In those scenarios, defenders often rely on conditional access signals, anomalous SSO patterns, mailbox rule changes, or unusual MFA events as reliable detection points.
In contrast, by initiating the session through the organization’s VDI, the threat actor effectively bypassed many of those detection strategies — appearing to downstream applications as a legitimate internal user with a trusted endpoint and enterprise IP. This creates a blind spot in detection because traditional identity protection and SaaS monitoring tools are tuned to flag risky external access, unfamiliar devices, and anomalous geographies; sessions originating from corporate VDI infrastructure often register as “normal” and trusted.
The attacker’s pivot to VDI demonstrates an awareness of existing defenses and a tactical evolution: rather than confronting hardened SaaS detection directly, they leveraged an implicitly trusted access path that erodes the effectiveness of conditional access policies and reduces anomalous telemetry, highlighting the need for defenders to correlate identity compromise signals across both identity recovery events and trusted internal access paths rather than treating them as separate domains.
Payroll platforms combine attributes attackers love:
As organizations harden endpoints and email, attackers will continue to pivot toward systems that assume legitimacy rather than enforce it.
The uncomfortable truth is this:
Payroll fraud doesn’t look like a cyberattack ... until the money is gone.
Over the past year, cybersecurity research and threat intelligence have shifted from treating payroll diversion as a niche fraud vector to recognizing it as a distinct and growing cybercrime category — especially where identity and HR systems intersect.
Although payroll diversion attacks have existed for years as a type of financial fraud, late 2024 marked a clear inflection point. In 2025, security research began identifying persistent, campaign-level activity specifically focused on SaaS HR systems like Workday — not just isolated scams. These schemes, characterized by social engineering, MFA manipulation, and direct account takeover, are now showing up in threat reports from major vendors and in industry advisories. This signals a structural shift: payroll systems have become first-class cyber targets, not afterthoughts.
Microsoft Threat Intelligence publicly documented financially motivated campaigns—tracked as Payroll Pirates—targeting SaaS HR platforms such as Workday to redirect employee paychecks. These attacks relied on phishing, MFA manipulation, and identity takeover rather than software vulnerabilities, signaling a shift toward identity-centric payroll abuse.
Identity providers and security vendors reported a rise in attackers directly targeting IT help desks to reset passwords and remove MFA protections, enabling downstream payroll changes. This method bypasses traditional phishing defenses and exploits human trust rather than technical weaknesses.
Industry guidance and HR security reporting increasingly highlighted payroll systems as high-risk assets, noting that self-service payroll changes and limited security telemetry make them attractive targets for attackers seeking fast, low-noise financial gain .
While payroll diversion is often categorized under broader BEC reporting, fraud advisories and state cyber alerts consistently flagged direct-deposit hijacking as a growing contributor to financial losses, reinforcing that this technique is no longer rare or isolated.
This isn’t just a security problem. It’s a business risk created by process design.
Organizations need to:
The next evolution of fraud won’t announce itself with ransomware notes or data leaks. It will arrive quietly, through valid logins, trusted systems, and routine workflows.
And for many organizations, the first sign will be an employee asking a simple question:
“Why didn’t I get paid?”
Detect when direct deposit or banking details are modified within a short window (e.g., 24–72 hours) after:
Alert when payroll systems are accessed from:
Especially valuable when paired with successful authentication, not failures.
Monitor for payroll access originating from:
Trusted access paths should raise scrutiny, not lower it.
Treat help desk–initiated actions as security signals, not routine IT noise:
These events often represent the true initial access phase.
Flag patterns where a user account:
This “check-in” behavior is common in fraud-driven attacks and rarely benign.